Aws application load balancer and Okta Oidc
In this article we will see how to add Okta authentication behind the Aws load balancer with Terraform.
Create the Okta Application
From Okta → Applications click on the Add Application and then Create New App
Select the Platform Web and OpenID Connect for Sign on method and click on Create
Once created you landing on the OpenId integration page
Name your application
The login redirect should be your DNS Record/oauth2/v1/authorize
lets say the record here is myrecord.okta.com
Once saved you will be on the App configuration page.
Let’s see some settings.
The grant type should be Authorization Code that means the code is returned from the Authorization Endpoint and all tokens are returned from the Token Endpoint.
Login redirect URIs → should be https://DNS/oauth2/idpresponse more information on https://docs.aws.amazon.com/elasticloadbalancing/latest/application/listener-authenticate-users.html
Logout redirect URIs → Can be your Okta tenant or whatever you want
Login initiated by → App Only
Initiated Login URI → You can directly put your application url to launch it directly from Okta
In the Client Credentials part you will find two importants informations that are used on the Load Balancer.
Client ID ⇒ The application identifier used on the header
Client secret ⇒ The secret is used to exchange the authorization code
Terraform configuration
Now we have our Okta application configured and we have to write our Aws configuration.
Firstly we create the Load Balancer follow the terraform doc about it : https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/lb
resource "aws_lb" "alb_test" {
name = "alb_test"
subnets = aws_subnet.public.*.id
internal = false
load_balancer_type = "application"
security_groups = [aws_security_group.lb_sg.id]
tags = {
Name = "alb_test"
Project = "production"
}
}
Once the Load balancer is created we can create the target group that we will reach.
Resource "aws_lb_target_group" "test_tg" {
name = "test_tg"
port = 80
protocol = "HTTP"
vpc_id = module.core.main.id
}
resource "aws_lb_target_group_attachment" "test_tga" {
target_group_arn = aws_lb_target_group.alb_test.arn
target_id = aws_instance.your_ec2_instance.id
port = 80
}
We can now create our Listener settings.
Remind A listener is a process that checks for connection requests, using the protocol and port that you configure. The rules that you define for a listener determine how the load balancer routes requests to its registered targets.
Firstly we create a listener on the http port and we redirect it on https
resource "aws_lb_listener" "lb_l_80" {
load_balancer_arn = aws_lb.alb_test.arn
port = "80"
protocol = "HTTP"
default_action {
// redirect to https
type = "redirect"
redirect {
port = "443"
protocol = "HTTPS"
status_code = "HTTP_301"
}
}
}
The listener http is redirected to the https listener that we will create
resource "aws_lb_listener" "lb_443" {
load_balancer_arn = aws_lb.alb_test.arn
port = "443"
protocol = "HTTPS"
ssl_policy = "ELBSecurityPolicy-2016-08"
certificate_arn = var.alb_certificate_arnWell now is time to create the default action remember the default action acting on default when we contact the Load balancer.
default_action {
type = "authenticate-oidc"
authenticate_oidc {
authorization_endpoint = "https://myrecord.okta.com/oauth2/v1/authorize"
client_id = 0oa6d4cqxdDaSPkTO357
client_secret = wYfvk4_DW_dBtnMTvf2Gv22EC0-Qhn6wDEBWHswn
issuer = "https://myrecord.okta.com"
token_endpoint = "https://myrecord.okta.com/oauth2/v1/token"
user_info_endpoint = "https://myrecord.okta.com/oauth2/v1/userinfo"
session_cookie_name = "AWSELBAuthSessionCookie"
session_timeout = "300"
scope = "openid profile"
on_unauthenticated_request = "authenticate"
}
}
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.test_tg.arn
}
}
We can take a look what is done on aws :
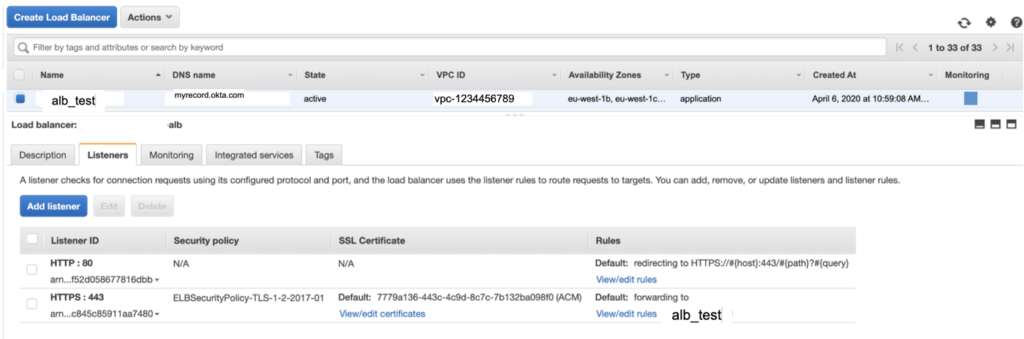
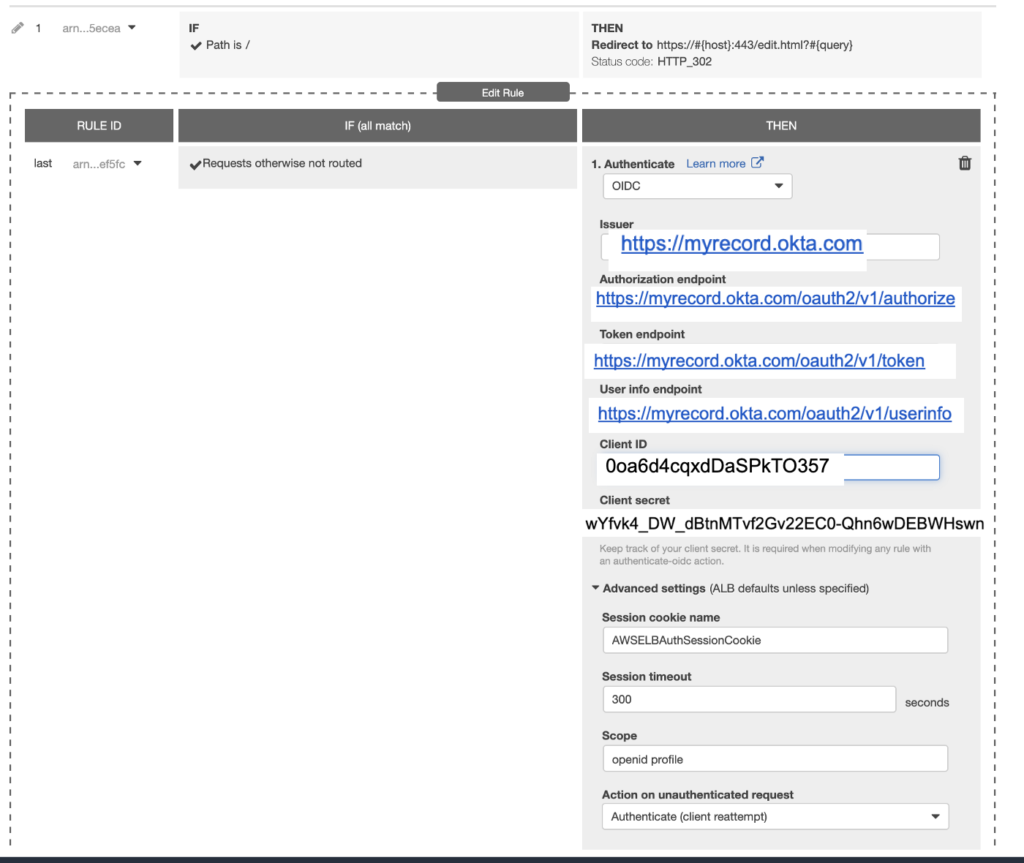
We have now finished when we will join the loadbalancer we will redirected to Okta. You can add some spécifics rules. Do note hesitate read more on https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/lb_listener_rule You are not limited on Okta Apps so you can create as many applications as rules on the loadbalancer.
Note If you note allowed to the application you will be have a 401 returned.
Thank you for reading !